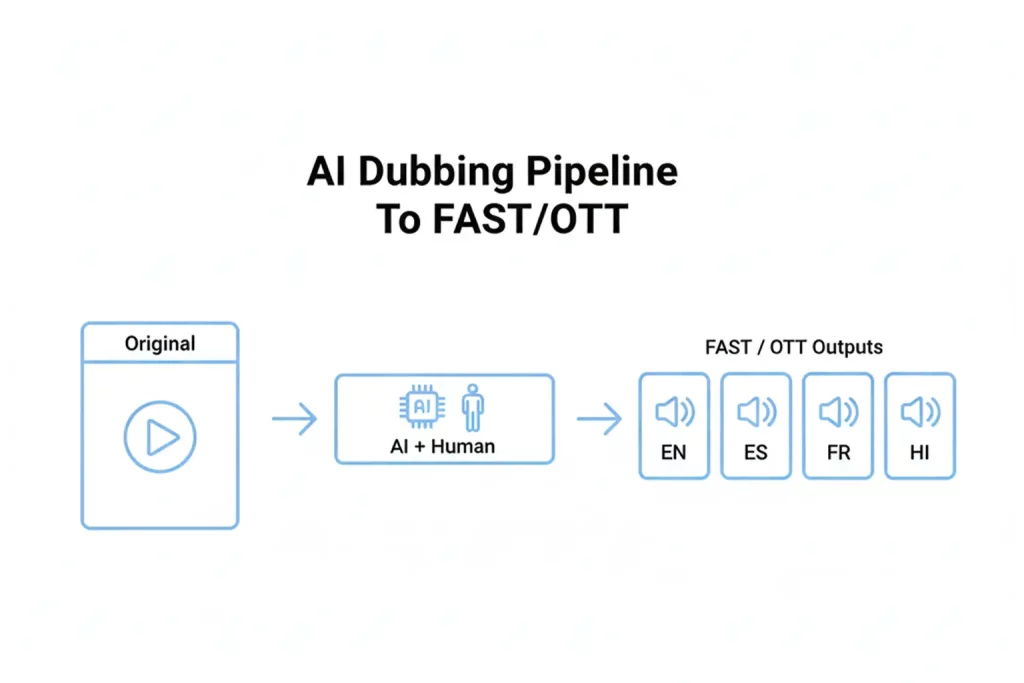
PAM integration cuts minutes from every handoff, which adds up to hours saved per show. Teams route ingest to bins automatically, assign tasks to editors without email, and push finished packages to air and to digital in one motion. Producers see status in one screen and stop chasing updates. Access control keeps privileged users honest, session monitoring guards critical assets, and compliance reporting proves that the team followed policy. You ship promos and full programs faster, with fewer errors and tighter security, even when people work remote inside cloud environments. This production workflow automation also supports cloud adoption and cloud governance. PAM connects on-premises server storage and SaaS tools, ties into your security infrastructure and SIEM, and gives DevOps clean hooks for automation. Build a tight security baseline from day one so account privileges stay right-sized, audit trail remains clear, endpoint security stays strong, and visibility improves across every stage. PAM software reduces the chance of data breaches and other cybersecurity threat patterns by keeping identities, assets, and workflows inside one accountable system. Keep reading to learn how PAM solutions deliver operational efficiency, enhanced security, and audit-ready management solutions for modern broadcast.
What Is PAM in a Broadcast Workflow?
A production asset management system sits at the center of day-to-day creative work. It tracks shots, graphics, project files, and versions while projects move from ingest to edit to delivery. You connect PAM to your editing suites, shared storage, archive, and newsroom tools so the whole system acts like one platform. This section defines PAM for media teams, clarifies the difference between PAM, MAM, and DAM, and frames where access management and identity management fit when you protect critical assets.

Defining Production Asset Management for Media Teams
Production asset management focuses on work in progress. Teams use a PAM solution to register new footage, create project structures, capture metadata, and route files to the right storage tier. PAM keeps track of who owns a task, who last touched a timeline, and which version goes to air. The system ties user access to roles, which gives editors what they need without exposing master accounts. Session management and session monitoring capture activity so supervisors can coach better habits and respond to incidents fast. With the right integration, PAM also triggers renders, file moves, and check-ins automatically, which keeps people creating instead of clicking.
How PAM Differs from MAM and DAM Systems
PAM handles live projects. A media asset management platform manages finished or near-finished media across programs, channels, and brands. A digital asset management system focuses on marketing content and brand files outside the broadcast chain. You often connect PAM to MAM and DAM to avoid duplicate effort. PAM owns the creation phase and passes mastered elements to MAM or a library after sign-off. MAM then publishes to playout, streaming, and social, while DAM feeds promo, sales, and corporate teams. This clear split lets you design access control for each stage, limit the attack surface, and keep compliance reporting focused and accurate.
What Is PAM Used For in Broadcasting?
PAM gives editors and producers one hub for media, projects, and tasks. It brings ingest, metadata, version control, and approvals into one flow that mirrors how shows actually get made. This section shows how teams use PAM to manage raw footage, share work across locations, and publish to many endpoints without reinventing the wheel for each format.
Managing Raw Footage, Graphics, and Project Files in One Hub
Teams register camera cards in PAM, which extracts timecode, codec, and slate data into searchable fields. The system links bins to shows, segments, and story slugs, which helps new staff find context fast. You track graphics packages, LUTs, and audio stems with the same rigor as video, so rebuilds take minutes instead of days. Version control locks the correct project file and reduces risk from duplicate timelines. You also keep proxy and high-res files in sync so remote editors cut on lower bandwidth while conform runs on shared storage.
Streamlining Collaboration Between Editors, Producers, and Remote Teams
PAM assigns tasks and due dates the moment material lands. Producers add notes once and stop pasting feedback into chats. Editors check in sequences, request graphics, and push approvals without breaking focus. Remote access works through identity management that maps users to roles and limits what they can change. Just-in-time access gives a temporary privilege for a specific job and then closes the window. Those controls limit risk without slowing anyone down.
Supporting Multi-Format Delivery Across Linear and Digital Channels
Your audience watches on cable boxes, apps, social feeds, and stadium screens. PAM tracks those deliverables as part of the project. It can render a clean feed, a captioned version, and platform-specific cuts without manual file wrangling. The system also writes delivery metadata that downstream systems need, including captions, ad markers, and content ratings. When you push to playout or to a cloud encoder, PAM logs the event, which simplifies compliance and incident response if something goes wrong.
Benefits of PAM Integration for Broadcast Teams
You integrate PAM to move faster with less risk. The right setup delivers faster turnaround, stronger content integrity, and cleaner audits. This section breaks down the benefits that matter to creative leads and engineering teams, including enhanced security for privileged accounts and streamlined reporting.
Faster Turnaround Times From Shoot to Air
Speed wins the day in live news, sports, and promo cycles. PAM removes manual steps that slow production. Editors receive bins that match the rundown, which eliminates wasted setup time. Producers approve in context, which cuts rounds of back-and-forth. Automated transcodes, renders, and deliveries clear bottlenecks. You spend more time crafting the story and less time managing files, so shows ship sooner and promos hit the right window.
Enhanced Security and Version Control for Critical Assets
Creative work moves faster when you protect it with the right guardrails. You assign user access based on roles and keep privileged identity separate from day edits. An access management solution tied to PAM enforces authorization, just-in-time access, and session monitoring. A password vault holds service credentials so no one shares application passwords or SSH keys in a chat. Privileged sessions run through session management so you can watch high-risk changes and roll them back if needed. Add endpoint privilege management and PEDM to reduce standing privileges on edit workstations. Feed security event data to your SIEM for threat detection and incident response. Rotate secrets on a schedule to reduce likelihood of privilege abuse. These controls reduce the attack surface, improve security posture, and keep your most valuable cuts and graphics secure without blocking the team.
Tie PAM to your identity infrastructure so infrastructure access management and privilege access policies work together. Map permissions to Microsoft groups where needed and separate domain service accounts from database accounts. Use vaulting for keys and tokens. Define account privileges that fit each role and log every change to the audit trail. For elevated work, rely on PIM privilege with time-bound role activation windows. Endpoint security tools add threat detection capabilities at the workstation layer so theft, malware attacks, or disruption attempts get stopped early. This blend of policy and tooling gives cybersecurity privileged teams the visibility they need without slowing editors.
Greater Operational Efficiency Through Automated Workflows
Automation gives teams more time to create. PAM tools watch for ingests and move files to the right volume. The system applies standard naming and folder structures that match your playbook. It spins up renders when a timeline hits a status and posts approvals where producers live. You can connect PAM to messaging so the right person gets a ping when a deliverable lands. That steady rhythm trims waste, reduces errors, and keeps projects on track.
Compliance and Audit Readiness for Regulated Content
Broadcasters answer to regulators and to partners. PAM integration gives you a clean record for who did what and when. Compliance reporting pulls user access, version history, and delivery logs into a simple export. If a sponsor asks for proof of placement, you retrieve the exact cut and the approval chain. If a regulator requests evidence, you show policy, access settings, and session logs. Map these exports to frameworks your business faces, including HIPAA and GDPR for certain segments, COPPA for kid-focused digital, or advertising standards in your region. Auditing teams want oversight into changes and deviations, security event data from SIEM, and proof of password rotation for superuser accounts. Document compliance requirements and audit requirements so reviewers see how privileges enforce your policies. You respond to incidents with facts, reduce compliance concerns, and improve the process based on data rather than guesswork.
Why You Should Integrate PAM Into Your Media Production Stack
PAM becomes more valuable as your team scales and your channel mix grows. Integration reduces errors, protects content integrity, and supports hybrid setups across on-prem and cloud environments. This section lays out the practical reasons to implement now rather than later.
Reducing Errors and Protecting Content Integrity
Every extra copy and every manual rename creates risk. PAM reduces that risk by enforcing a single source of truth for project files and media. Editors check out timelines instead of cloning them. The system locks approved versions, which keeps accidental changes out of air masters. Access control separates privileged users from general staff. You keep credentials in a password vault and gate sensitive actions with approvals. The result is clean, traceable work that stands up to sponsor, legal, and standards reviews.
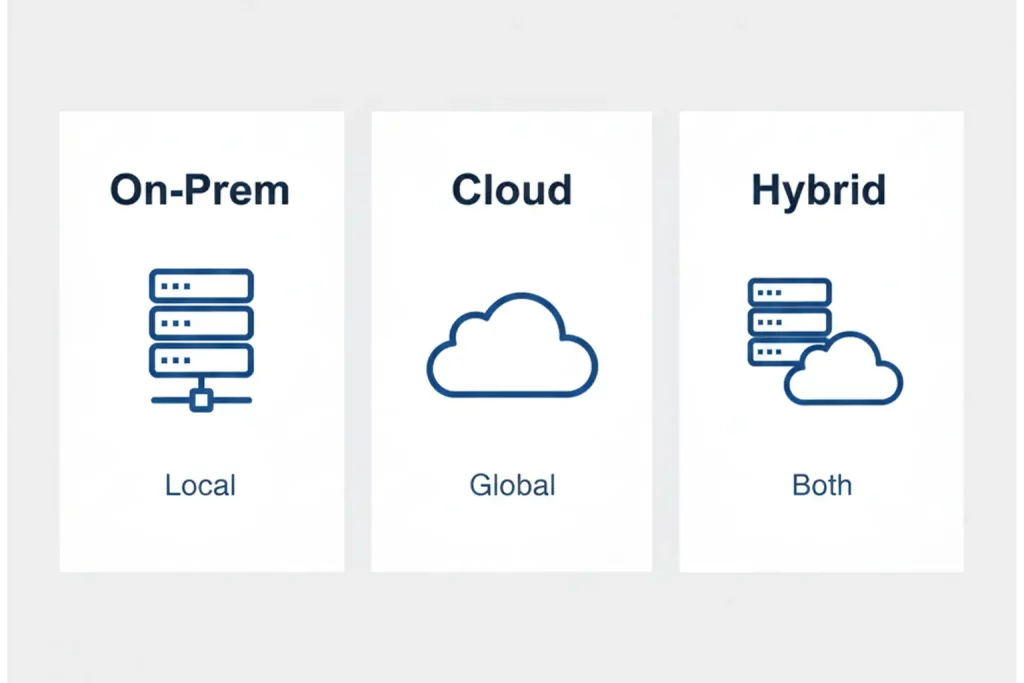
Simplifying Remote and Cloud-Based Production Environments
Remote and cloud production expand your reach and your risk. PAM brings order to this sprawl. You connect cloud storage and on-prem tiers under one project view. Identity management grants remote access through roles, not by sharing admin accounts. Just-in-time access opens a narrow window for a task and then closes it. Session monitoring captures actions so you can coach, review, and correct. Tie PAM to your security infrastructure so cloud adoption stays safe across SaaS, servers on company premises, and mixed workloads. Align system configuration and architecture with your cloud governance standards to keep deviations low while editors work at full speed. Plan deployment in phases so teams adapt without disruption and your security baseline holds across regions.
Creating a Scalable Foundation for Future Content Demands
Your show count, your formats, and your platforms will keep growing. PAM lets you scale without chaotic folders and email approvals. You add more editors and more deliverables without losing track of who owns what. Integrations with MAM, newsroom, graphics, and archive systems give you a clear handoff from creation to distribution to long-term storage. When your team makes a new show or launches a new platform, you adjust templates instead of rebuilding the pipeline.
Implementing PAM Integration Step by Step
You set up PAM once and then keep tuning it as your slate evolves. A clear plan avoids missteps and teaches the team how to work in the new flow. This section gives a practical path from assessment to rollout, including how to choose a PAM solution and how to tie it into editing, storage, and archive.
Assessing Current Tools and Identifying Gaps in Workflow Automation
Start by mapping the real path a clip takes today. Track every stop from ingest to edit to delivery. Write down where people wait, rename files, or request access. Those gaps mark the first targets for automation. Collect requirements from editors, producers, audio, engineering, and DevOps. Align on roles, user access, and remote access rules. Decide where identity management and access control sit, and list which privileged accounts, superuser accounts, SSH keys, and application passwords need extra protection. Inventory identity infrastructure, including Microsoft directories and SSO. Log system configuration and architecture details so the integration process starts with facts and ends in clean completion, user onboarding, and adoption. Share findings widely so leaders gain visibility into the plan.
Choosing the Right PAM Solution That Fits Broadcast Needs
Look for a PAM solution built for media production. Focus on project templates, bin automation, version control, and tight connections with your NLEs and graphics tools. Check that it supports cloud environments, durable APIs, SSO, and integration with your authentication system and multi-factor authentication. Confirm that the access management solution integrates with your directory so you can drive access from groups and roles. Evaluate PAM software features and PAM solutions processes that govern request, authorization, approval, completion, and auditing, and verify they uphold the least privilege principle. Ask for capabilities like session monitoring, endpoint security controls, endpoint privilege management, time-boxed role activation, and detailed compliance reporting. Ensure threat detection capabilities connect to your SIEM. Map designs to infrastructure access management and privilege access policies. Many vendors call this stack PAM, PASM, PIM privilege, or PEDM. Whatever the label, your team will move faster when the system matches how they already work and when admin control fits your security posture.
Integrating PAM With Editing Suites, Storage, and Archive Systems
Connect PAM to your NLEs so editors can check in and check out sequences without leaving the timeline. Tie in shared storage and tiers for proxy and high-res so conform happens without manual moves. Link your archive so finished shows and assets flow out with complete metadata. Connect newsroom systems for rundowns and slugs, and graphics systems for lower thirds and full frames. Wire alerts to chat or email so the right people see status without asking. Treat credential management as part of integration, which means service accounts sit in a password vault and use limited scope. Feed PAM logs to your SIEM so threat detection watches privileged sessions in real time. Plan deployment as a staged rollout so baseline controls hold and teams avoid disruption.
Metadata, Tagging, and Search Features That Save Hours in Post-Production
Metadata makes the whole system searchable. Build templates with fields for show, segment, location, rights, and talent. Capture speech-to-text and on-screen text so editors can jump to quotes without scrubbing. Keep the workflow simple so each tech tool helps, not hinders. Use controlled vocabularies so producers get consistent results. Add logo and face detection where it helps compliance. Expose search in places where people already work, not in a separate portal. Track website and web page deliverables in the same project so digital teams can publish fast with the correct versions and captions. Capture user data that relates to publishing roles and keep customer data out of creative tools to reduce risk.
Endpoint Privilege Management, SSH Keys, and Vaults in Media Workflows
Workstations and render nodes handle critical assets every day. Reduce risk by applying the least privilege principle on endpoints. Replace standing privileges with just-in-time elevation using endpoint privilege management or PEDM. Store SSH keys, application passwords, and service credentials in vaults and enforce password rotation. Limit admin control to a small set of authorized users and log every privileged session. Your SIEM ingests security event data so you spot insider threats, insider misuse, malware activity, and cyberattacks before they spread. Pair these steps with endpoint security controls so data breaches get blocked early. This approach cuts security complexity without slowing the team and keeps workloads clean across on-premises and cloud.