Broadcasters must keep airtight audit trails to prove regulatory compliance, resolve disputes, and guard against security threats. Audit logs capture every access, system change, and user activity in real time, ensuring broadcasters can prove adherence to FCC rules, PCI DSS, GDPR, and other compliance requirements. Broadcast compliance monitoring systems extend this protection by providing log data, real-time alerts, and tamper-proof records. Staying legally protected means adopting structured log management, retention policies, and security controls that make every log trustworthy and accessible when regulators come knocking.
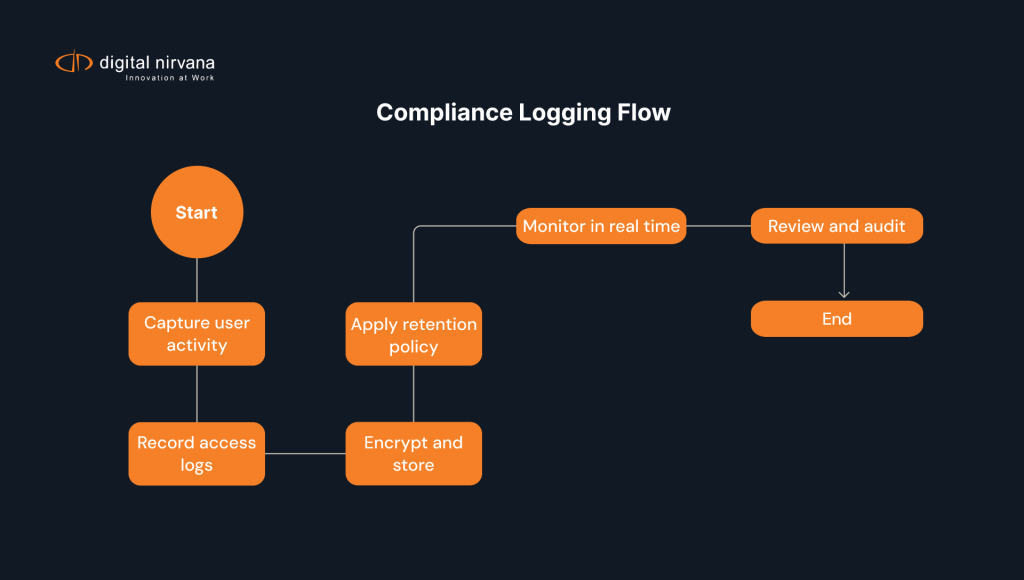
Regulatory compliance and broadcast audit logs made simple
Compliance logging forms the backbone of a broadcaster’s legal protection and regulatory compliance program. Audit logs record data access, user activity, authentication permissions, and security events, giving regulators a transparent view of operations. In broadcasting, these logs prove that content aired complies with FCC rules, licensing restrictions, and data protection regulations. A strong audit trail also allows faster dispute resolution when challenged by advertisers or regulators. By integrating audit logging, compliance audits, and log monitoring requirements into daily workflows, broadcasters ensure compliance requirements are consistently met. For more insight into monitoring compliance, explore Digital Nirvana’s Broadcast Monitoring Services.
Why Digital Nirvana supports compliance logging for broadcasters
Our services at Digital Nirvana help broadcasters streamline compliance programs with tools designed for accuracy, security, and ease of use. Products like MonitorIQ and MetadatalQ simplify the collection and review of audit logs, ensuring immutability and accountability. From log retention strategies to real-time alerts, we provide broadcasters with the solutions they need to meet FCC and PCI DSS requirements while protecting personal data. At Digital Nirvana, we focus on building compliance programs that integrate seamlessly into broadcast operations.
Audit logs vs. regular system logs: what’s the difference?
Audit logs and system logs often get confused, but each plays a distinct role in compliance and security. System logs record routine operations such as device IDs, workload performance, or optimization data, while audit logs focus on compliance requirements and log integrity. A deeper understanding can be found in Digital Nirvana’s blog on audit logging best practices.
Defining audit logging and how it differs from general logs
General logs capture technical details such as configurations, error codes, or system uptime. Audit logs capture user activity, accountability measures, and compliance aspects. The key difference lies in purpose: system logs support IT operations, while audit logs support compliance and legal protection.
When to rely on access logs, user activity, or system logs
Access logs track who accessed which folder or system. User activity logs detail what they did. System logs capture background activity like deletion events or optimization performance. Audit logs combine these to form authoritative records. For a closer look at how audit logs intersect with other forms of monitoring, see Digital Nirvana’s blog on monitoring and compliance.
Why log integrity and tamper-proof trails matter for compliance
Regulatory compliance requires audit logs to remain immutable. A log with altered timestamps or missing usage data cannot stand up to regulatory audits. Immutability, encryption, and clear accountability structures ensure audit trails remain verifiable. U.S. agencies such as the Federal Communications Commission (FCC) provide compliance guidance requiring tamper-proof records.
The tools needed for audit log best practices in broadcast operations
A structured approach to log management protects broadcasters from compliance gaps. Scalable tools collect, analyze, and secure audit logs. Centralized logging, encryption, and SFTP strategies support effective compliance.
Choosing scalable log management tools (structured logging, centralized log collection)
Log management tools bring together data from multiple broadcast systems into one dashboard. Structured logging ensures consistency, while centralized collection simplifies compliance audits and log review. Broadcasters can reduce complexity by standardizing configurations and ensuring accountability.
Leveraging cloud-based platforms like Google Cloud for secure log storage
Cloud SIEM and storage platforms offer encryption, tiered storage, and immutability for logs. Google Cloud and other providers secure logs against tampering, physical damage, or deletion errors. Cloud tools also support advanced analytics for compliance.
Securing log data with encryption, access control, and integrity checks
Logs must remain confidential and tamper-proof. Encryption safeguards logs in transit and at rest. Access control ensures only authorized personnel can view or modify logs. Integrity checks verify completeness. Accountability mechanisms and compliance audits make logs defensible in regulatory reviews.
Using audit logging for security and compliance in broadcasting
Audit logging strengthens both compliance and data security by detecting anomalies and supporting incident response. Broadcasters can also leverage advanced compliance monitoring solutions like MonitorIQ for centralized visibility.
How audit logs reveal security events, unauthorized access, and compliance gaps
Audit logs capture suspicious login attempts, IP addresses, usage data, and workload anomalies. Non-compliance and unauthorized deletion of folders or files are flagged quickly. These insights help IT teams respond before damage occurs.
Implementing log monitoring, retention policies, and regular log review
Monitoring tools track activity in real time. Retention policies define how long logs remain accessible. Regular review of configurations, usage data, and policy updates ensures compliance. Automation reduces complexity and makes compliance programs more resilient.
How broadcast compliance monitoring systems collect logs in real-time
Monitoring tools collect logs from multiple systems, including metadata, traffic, and SFTP transmissions. They track auditing events, folder-level access, and policy changes. Real-time log monitoring ensures accountability. For insights into automation, see Digital Nirvana’s blog on AI-driven compliance checks.
Log retention and review: meeting PCI DSS and other regulatory requirements
Retention policies form the foundation of compliance logging. PCI DSS, GDPR, HIPAA, and FCC rules all dictate retention standards.
Understanding logging requirements: PCI DSS, GDPR, HIPAA in broadcast contexts
PCI DSS requires audit trails for payment data systems. GDPR requires user activity and personal data access logs. HIPAA requires healthcare information logs. Each regulation mandates specific retention practices. The U.S. Department of Health & Human Services provides HIPAA-specific retention requirements.
Setting retention policies: how long to retain audit logs and access logs
Retention varies. PCI DSS requires one year of audit logs, HIPAA up to six years, and GDPR may require longer. Retaining logs beyond requirements adds security and supports accountability.
Automating log review and analysis for proactive regulatory compliance
Automated analytics flag anomalies across usage data, user email, and system configurations. Automation reduces workload and improves completeness of compliance audits.
Harnessing real-time compliance monitoring in broadcast workflows
Real-time monitoring transforms compliance from reactive to proactive.
What broadcast compliance monitoring looks like: AI-driven content checks, metadata logging
AI systems analyze usage data, email messages, and metadata logs for restricted or non-compliant content. These systems log every compliance aspect for audit readiness.
Building an audit trail during live broadcast with automated alerts
Automated alerts notify teams of non-compliance in folders, ad workflows, or spectrum logs. Audit trails created during live events prove accountability and support compliance audits.
Integrating compliance logging into traffic and ad-insertion systems for seamless workflows
Logs integrated into ad systems prove ad delivery and payment data tracking. This protects both revenue and compliance obligations.
Common challenges and how to resolve them in compliance logging
Broadcasters face challenges like high log volumes, fragmentation, and timestamp inconsistencies.

Dealing with log volume and storage costs strategies for compression and tiered storage
Logs from email, policy updates, and apps generate huge volumes. Broadcasters can use compression, tiered storage, and export strategies to control costs while staying compliant.
Avoiding log fragmentation by centralizing log collection and analysis
Fragmentation across Microsoft tools, SharePoint, or datadog integrations creates compliance risks. Centralizing logs improves accountability and audit readiness.
Ensuring timestamp accuracy and log correlation across systems
Accurate timeline management ensures consistency across data centers. Misaligned timestamps undermine audit trails. Synchronizing ensures logs stand up in audits.
Additional resources to strengthen your compliance logging framework
Strong programs rely on frameworks, tools, and team development.
Reference frameworks: NIST SP 800-92, PCI DSS, GDPR, and broadcast-specific rules
NIST SP 800-92 provides log management best practices. PCI DSS and GDPR outline strict requirements. Broadcasters should align compliance audits with these frameworks.
External tools and audit logging guidelines for broadcasters
External audit logging software, SFTP tools, and analytics platforms provide added support. FCC guidelines highlight compliance aspects specific to broadcasting.
Developing your team: documentation, training, and establishing roles for log review
Training staff to manage configurations, deletion events, and accountability processes ensures compliance remains strong. Documenting procedures helps staff remain audit-ready.
Why choose Digital Nirvana for compliance monitoring
At Digital Nirvana, we help you strengthen compliance logging by offering advanced solutions for monitoring, metadata management, and secure storage. Our MonitorIQ platform ensures audit trails remain complete, immutable, and legally defensible. Paired with Media Services and Trance, our solutions support compliance requirements across global broadcast operations. By working with us, you gain a partner focused on compliance, accountability, and data security.
In summary, compliance logging in broadcasting
Compliance logging protects broadcasters from fines, lawsuits, and reputational harm. Key practices include:
- Maintain audit trails that track user activity, payment data, and folder access
- Centralize log collection to reduce complexity and improve accountability
- Use encryption, immutability, and access controls to protect logs
- Automate monitoring, analytics, and compliance audits
- Align policies with PCI DSS, GDPR, HIPAA, and FCC rules
- Integrate logging into ad systems and metadata workflows
- Address storage, deletion, and timestamp challenges proactively
Compliance logging secures trust, accountability, and operational continuity. Broadcasters who adopt best practices build systems that withstand audits and regulatory scrutiny.
FAQs
What is the difference between an audit log and a system log?
Audit logs record compliance-related activity like access, email, or payment data. System logs record technical performance like workload or optimization data.
How long should broadcasters retain audit logs?
Retention varies: PCI DSS requires one year, HIPAA up to six years, and GDPR may require longer. Broadcasters should align retention with regulatory requirements and business accountability.
Why is log integrity critical for compliance?
Log integrity ensures completeness and immutability. Regulators require tamper-proof logs as evidence. Controls such as encryption, SFTP transfers, and strict accountability protect integrity.
How does real-time compliance monitoring help broadcasters?
Real-time monitoring builds audit trails during live broadcasts. Automated alerts flag compliance gaps in folders, ad workflows, or usage data, reducing liability.
What are the biggest compliance logging challenges for broadcasters?
Challenges include handling log volume, fragmentation across Microsoft or SharePoint, and maintaining timestamp accuracy. Centralized collection, automation, and clear accountability solve these issues.