Distributed master control sounds modern until something breaks at 2 a.m. across three time zones. Then the real question shows up fast: can your monitoring stack tell you what happened, where it happened, and give you proof without a scramble?
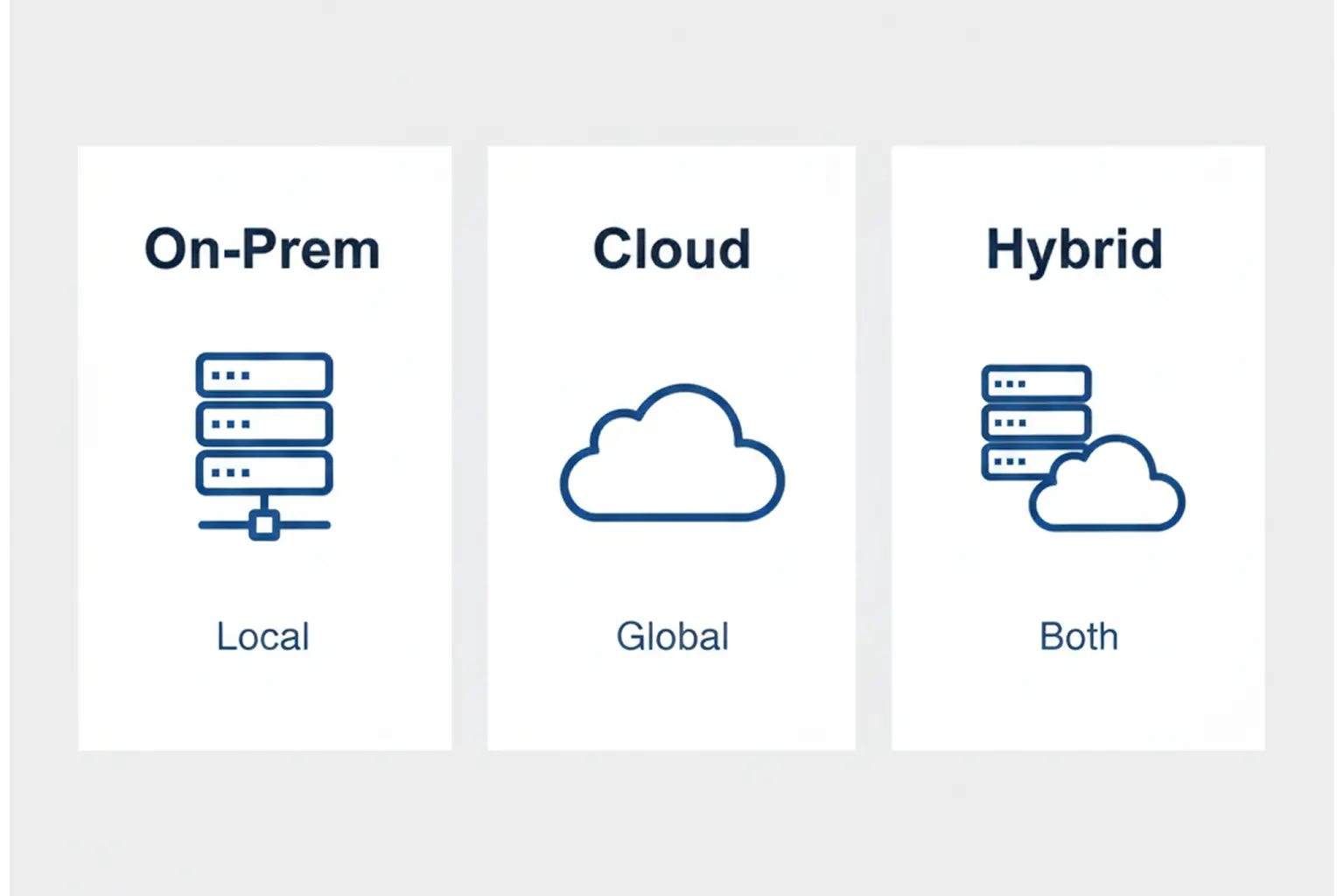
Broadcast media monitoring tools are no longer only about watching a clean linear output. Master control monitoring now spans multiple distribution paths, multiple facilities, and often multiple formats, from SDI to OTT to managed IP. The architecture you choose, on-prem, cloud, or hybrid, determines how quickly you detect issues, how reliably you can record proof, and how well teams can collaborate when operations are distributed.
This guide explains the practical differences and gives you a blueprint for choosing the right architecture.
What “Distributed Master Control” Changes
Distributed master control typically means at least one of these realities:
- Channels originate in one place but are monitored and managed from another
- Playout, branding, and distribution are split across sites
- You operate linear and streaming outputs in parallel
- Operators, engineering, compliance, and ad teams need shared access to the same evidence
That is why cloud-based master control discussions emphasize flexibility, orchestration, and deeply integrated monitoring, rather than bolt-on solutions afterward.
In monitoring terms, the biggest change is this: you need consistency across locations, and you need a shared record of truth that multiple teams can access without exporting files all day.
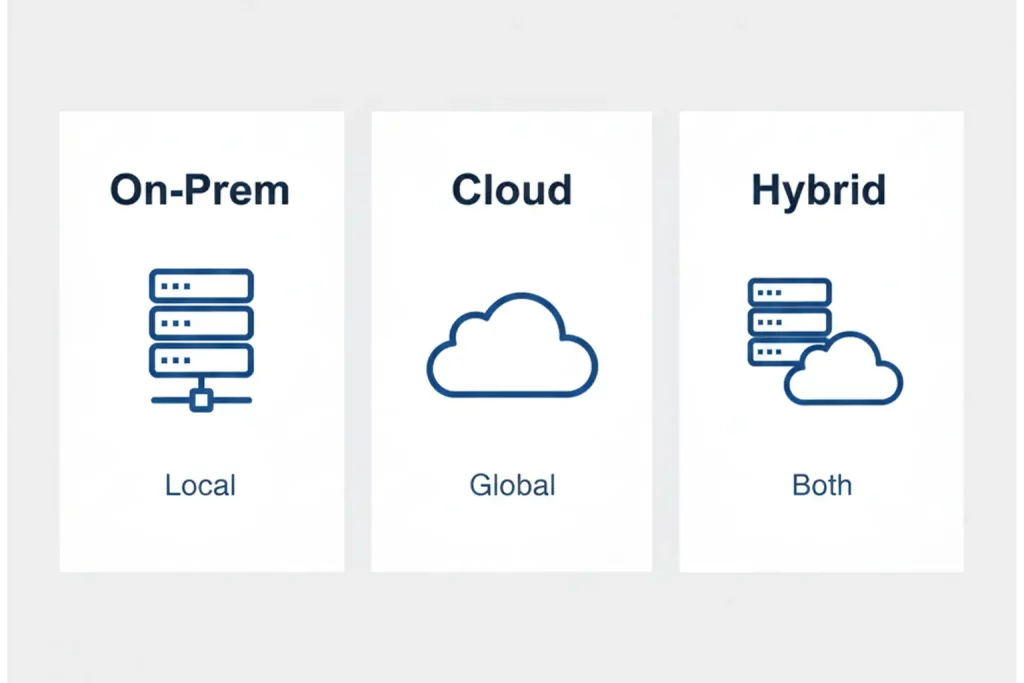
On-Prem Monitoring Architecture
What It Looks Like
On-prem monitoring is usually built around capture and recording close to the signal, then local storage and local operator workflows.
Typical components:
- Ingest and recording appliances in the facility
- Local multiview and alarm dashboards
- Local retention storage and exports
- Integration with facility systems and workflows
Where On-Prem Works Best
- Single-site operations where most signals are local
- Environments with strict data residency, network isolation, or highly controlled workflows
- Operations that require predictable low latency inside the facility
Tradeoffs You Feel In Distributed Operations
- Remote access and cross-team sharing can become slower and more fragmented
- Scaling for pop-up channels or new outputs often means new hardware projects
- Disaster recovery and redundancy can be expensive if built as full mirrored sites
On-prem can still be right, but once master control becomes distributed, the operational friction tends to show up in access, scale, and proof workflows.
Cloud Monitoring Architecture
What It Looks Like
In cloud-first monitoring, the control plane and, often, the recording plane live in the cloud, with feeds arriving via contribution protocols or through cloud playout and packaging paths.
This model pairs well with cloud master control strategies, where systems are orchestrated as software and scaled dynamically.
Where Cloud Works Best
- Streaming-heavy operations where the “real signal” is the packaged stream
- Rapid channel launches, seasonal expansions, and pop-up events
- Teams are distributed across regions that need fast shared access
Tradeoffs You Must Design For
- Bandwidth and reliability of contribution paths
- Latency, especially if operators expect near real-time confidence monitoring
- Cost control, especially storage and data transfer patterns in always-on recording
- Security, identity, and audit requirements across multiple teams and partners
Cloud monitoring can be extremely effective, but only if you treat recording, retention, and access patterns as first-class architecture decisions, not afterthoughts.
Hybrid Monitoring Architecture
A hybrid is often the most practical answer for distributed master control because it separates two truths:
- Capture needs to be close to the signal
- Collaboration and governance need to be shared across locations
Hybrid cloud monitoring is commonly defined as monitoring that spans private and public environments, including edge locations and CDNs.
What It Looks Like In Broadcast Monitoring
- Capture nodes on-prem at facilities, ingest points, or partner handoffs
- Centralized dashboards accessible to distributed teams
- Recording stored locally, in the cloud, or split by retention tiers
- Unified alerting rules and audit history across the whole footprint
This also aligns with broader hybrid monitoring patterns, such as a single pane of glass for centralized access or segmented architectures that separate sensitive data and operational data for compliance.
Why Hybrid Wins in Distributed Master Control
- You can keep deterministic capture where it matters
- You can enable cross-team access without VPN gymnastics
- You can tier storage and retention for cost control
- You can implement better DR by using cloud elasticity without fully abandoning on-prem
Hybrid also reduces the “visibility problem” that shows up when teams rely on separate native tools across environments, creating blind spots and slower troubleshooting.
Architecture Decision Matrix
| Factor | On-Prem | Cloud | Hybrid |
| Distributed Operations | Harder | Strong | Strong |
| Scale and Pop-Up Channels | Slower | Fast | Fast |
| Low-Latency Confidence | Strong | Depends | Strong where needed |
| Shared Proof and Collaboration | Depends on exports | Strong | Strong |
| Retention Cost Control | Predictable hardware cost | Needs active management | Flexible with tiering |
| Compliance and Governance | Strong locally | Strong with good controls | Strong with segmentation options |
| Multi-Format Environments | Strong in facility | Strong for OTT | Strong across both |
A Reference Blueprint For Distributed Master Control
Layer 1: Capture Close To Truth
- Linear: capture at the facility output and any critical downstream handoff
- Streaming: capture at origin and at least one return-path viewpoint if QoE or partner disputes matter
- IP facilities: monitor timing and stream health where ST 2110 flows live, because ST 2110 treats video, audio, and ancillary as separate streams that must remain synchronized
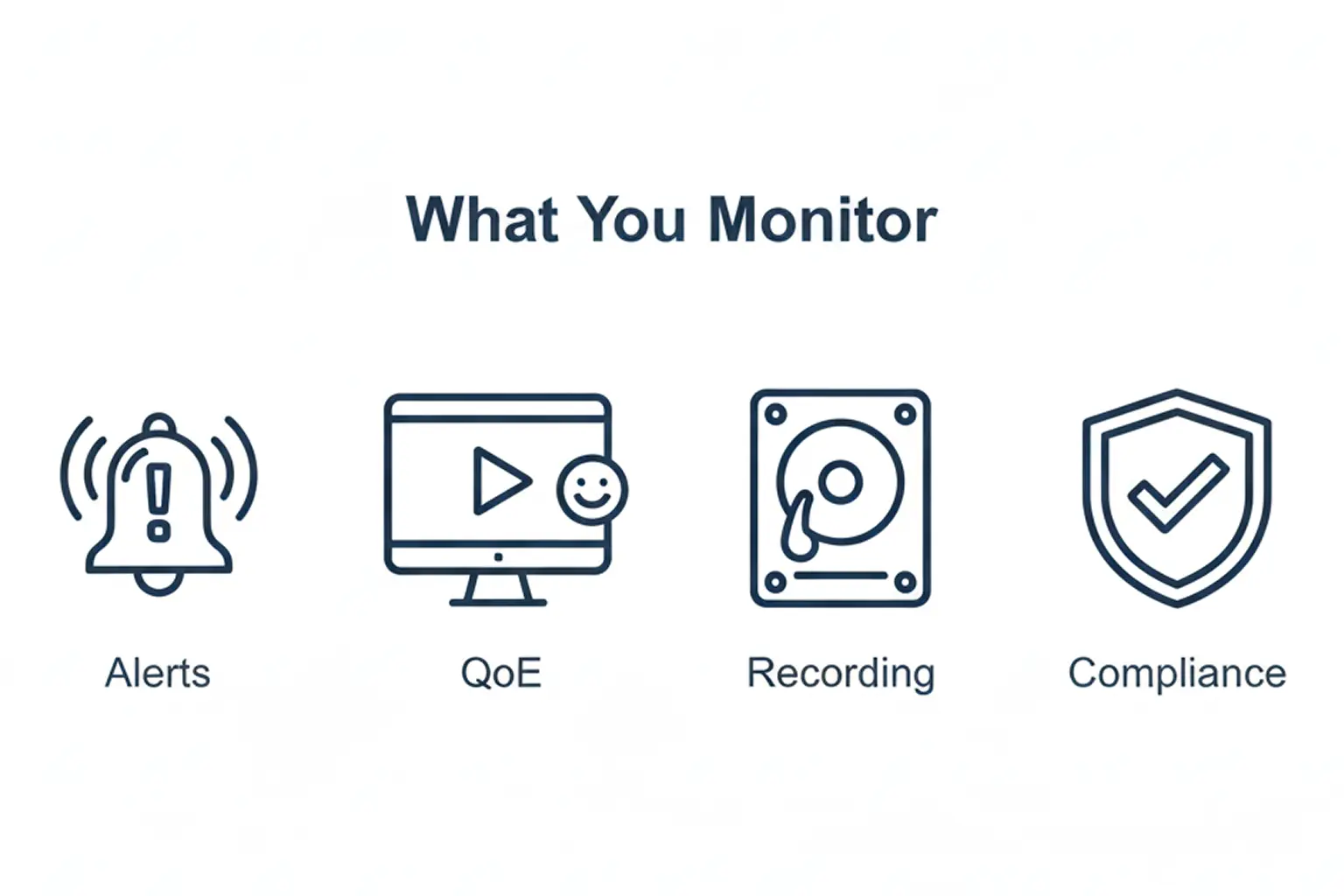
Layer 2: Normalize Alerts Across Sites
Build alerting as a shared language:
- Signal integrity and availability
- Compliance rules like captions and loudness
- Ad verification and proof-of-performance checks
- QoE alarms where streaming experience is the KPI
Layer 3: Centralize Evidence, Not Just Dashboards
Distributed master control fails when the evidence is trapped in the wrong place. Design for:
- Timecoded review
- Fast clip creation
- Controlled sharing across departments and vendors
- Audit visibility, so decisions can be traced later
Where MonitorIQ Fits
If your goal is to unify monitoring, compliance logging, and proof workflows for distributed teams, MonitorIQ positions itself as a single platform that addresses ad verification, QoE monitoring, and compliance logging, with loudness and caption monitoring, and includes real-time alerting.
Digital Nirvana also describes MonitorIQ as recording from points across the delivery chain and aligning video, captions, loudness, SCTE, and other metadata to a single timecoded timeline, which directly supports distributed investigations and proof workflows.
For additional context that supports a commercial evaluation:
- Content monitoring and unified evidence workflows for broadcasters
- Compliance monitoring expectations and cross-team access patterns
- Brand and content oversight use cases in the same monitoring surface
FAQs
They are monitoring, alerting, and recording systems designed to give distributed teams visibility into channel outputs, compliance signals, ad events, and viewer-impact issues, with timecoded evidence that can be searched and shared.
On-prem monitoring is typically closest to facility signals and offers predictable local performance. Cloud monitoring emphasizes global access, elasticity, and faster scaling, but depends more heavily on network paths, storage strategy, and governance design.
Hybrid lets you capture close to signals while centralizing access, alerting, and evidence across locations. It also helps manage complexity and visibility when environments span on-prem and cloud.
You monitor both what operators see and what the network must maintain: separate essence streams and their synchronization. ST 2110 is designed around separate elementary streams over IP that are individually timed and must remain aligned.
At minimum: real-time alerting, timecoded recording, compliance checks like captions and loudness, ad verification, and cross-team access with proper permissions.
Conclusion
The “right” architecture is the one that keeps master control fast during incidents and credible during disputes. On-prem remains strong for single-site determinism. Cloud wins for speed and scale. Hybrid is often the best fit for distributed master control because it combines close-to-signal capture with centralized access, alerting, and evidence workflows.
Key Takeaways:
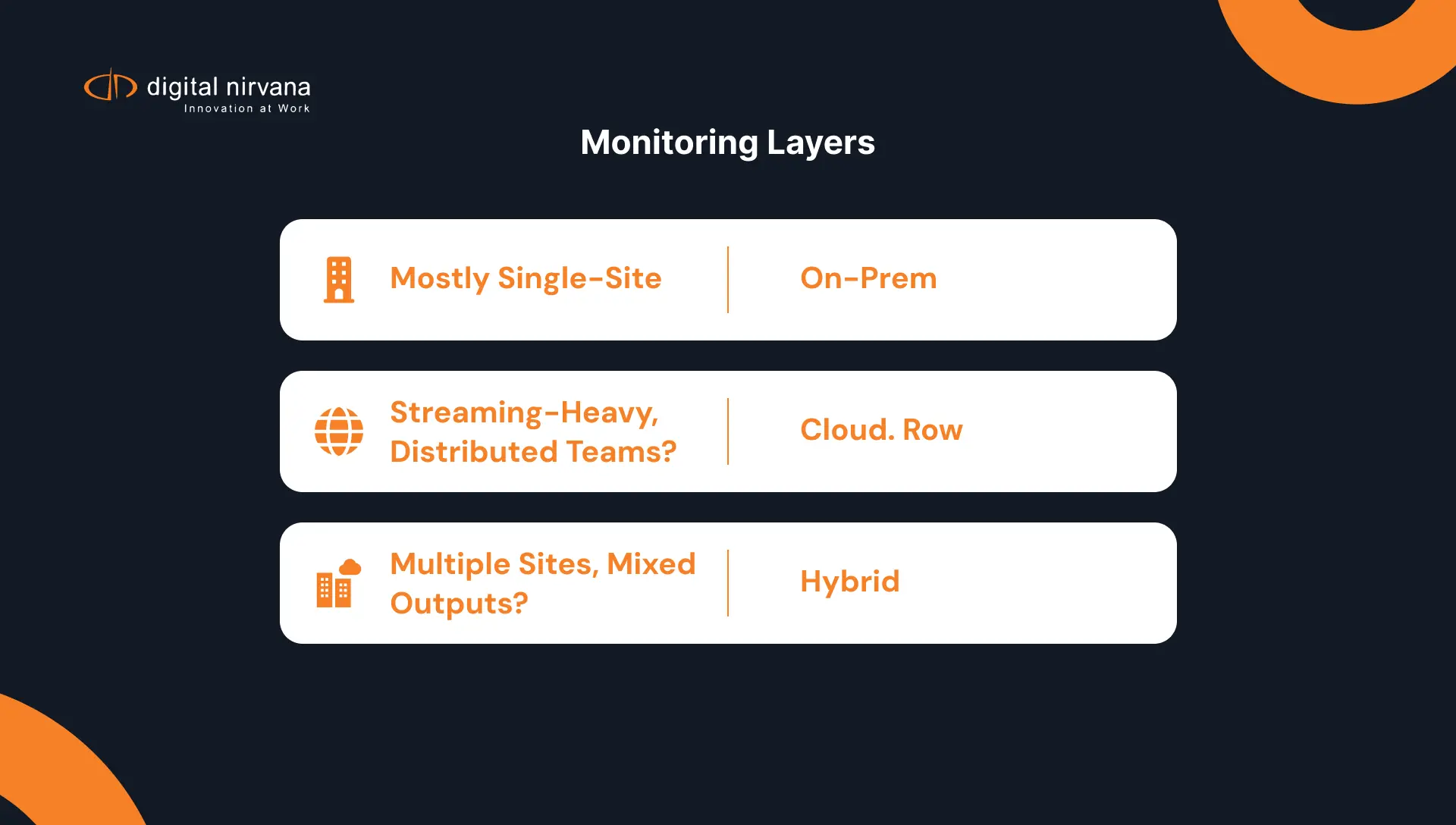
- Choose on-prem if your operation is mostly single-site and signal-local, with strict control requirements.
- Choose cloud if your operation is streaming-heavy and built around rapid scaling and distributed access.
- Choose hybrid if you need consistent monitoring, shared evidence, and cost-flexible retention across multiple sites and outputs.
- For distributed master control monitoring, prioritize timecoded evidence, cross-team permissions, and unified alerting over “more dashboards.”
- If you want one platform that ties monitoring, QoE, ad verification, and compliance logging together, evaluate MonitorIQ against your on-prem, cloud, and hybrid requirements.